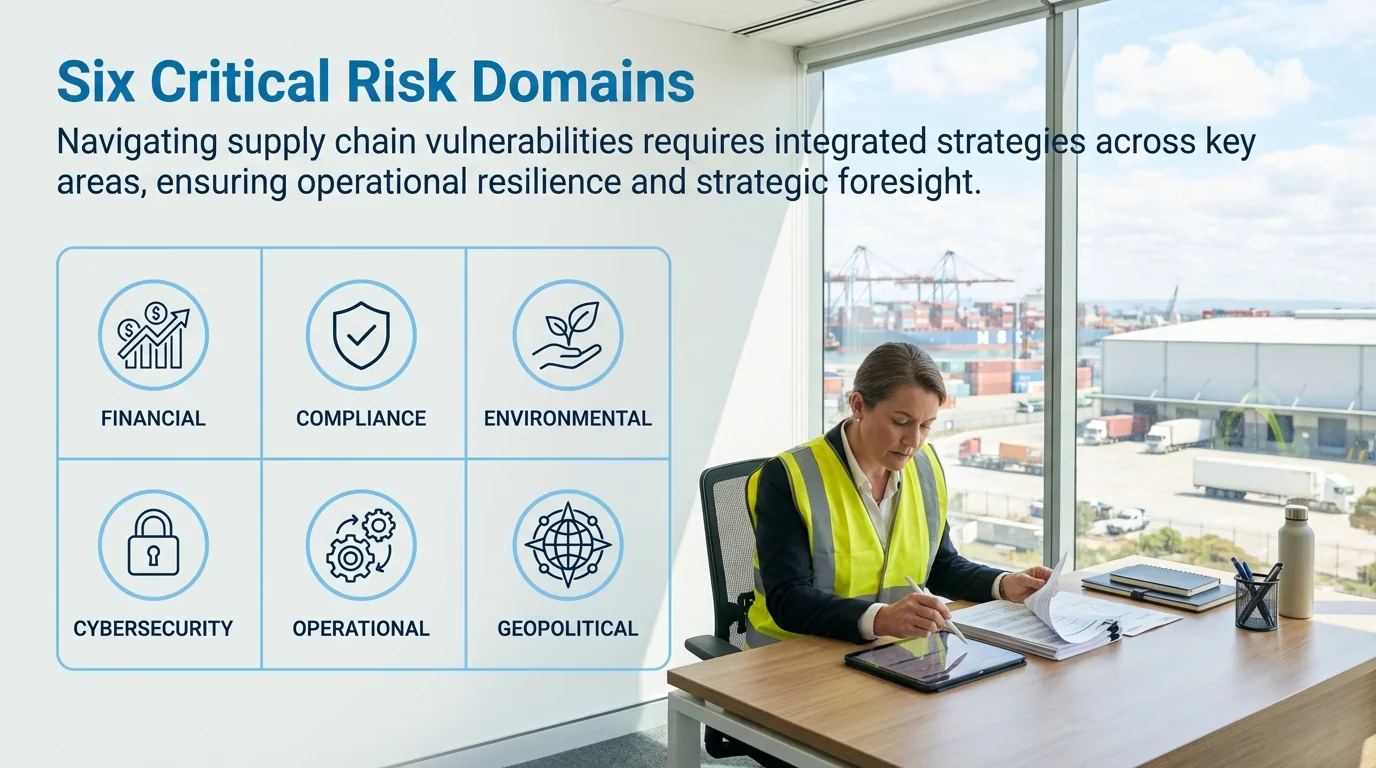
Effective supply chain risk management starts with a systematic checklist that addresses six critical risk domains. Financial instability, regulatory non-compliance, environmental gaps, cybersecurity vulnerabilities, operational disruptions, and geopolitical threats all demand structured assessment protocols that protect your supply network from cascading failures.
The best risk management checklists don’t just identify problems. They create repeatable frameworks for evaluation, scoring, and response across your entire supplier base.
Organizations operating transport-dependent supply chains face unique compliance pressures under frameworks like Australia’s Heavy Vehicle National Law. Your checklist must balance regulatory requirements with practical risk mitigation strategies that keep operations running smoothly.
This guide provides a practical checklist framework built on 25 years of supply chain experience managing FMCG networks across Australia and the UK. You’ll get specific assessment criteria, scoring models, and monitoring protocols that turn risk identification into proactive management.
What Is a Supply Chain Risk Management Checklist?
A supply chain risk management checklist is a structured tool for identifying, evaluating, and monitoring vulnerabilities across your supplier network. It provides repeatable assessment criteria that ensure consistent risk evaluation throughout your supply chain.
The checklist approach works because it standardizes how you assess supplier risk. Instead of relying on individual judgment, your team follows documented protocols that capture financial health, operational capability, compliance status, and security practices.
Professional risk assessment requires examining multiple risk categories simultaneously. Organizations should identify risks across multiple domains including financial instability, non-compliance, ESG gaps, cyber vulnerabilities, and geopolitical disruptions.

Your checklist becomes the foundation for supplier due diligence. Each assessment generates documented evidence of your risk management process.
Key Components of Effective Checklists
Risk assessment checklists need clear evaluation criteria for each risk category. Specific questions, required documentation, and acceptance thresholds prevent subjective assessments that miss critical vulnerabilities.
Scoring mechanisms turn qualitative observations into quantitative risk ratings. Consistent scoring models allow you to compare suppliers objectively and prioritize resources toward your highest-risk relationships.
Documentation requirements ensure your due diligence process creates audit trails. Certification verification, financial records, insurance documentation, and compliance evidence all belong in your checklist framework.
The strongest checklists include time-based review triggers. Supplier risk changes over time, so your framework needs scheduled reassessments plus event-triggered reviews when supplier circumstances change.
Why Supply Chain Risk Assessment Is Critical
Supply chain disruptions create cascading problems that extend far beyond delayed deliveries. Financial losses, regulatory penalties, safety incidents, and reputational damage all stem from unmanaged supplier risks.
Organizations without structured risk assessment operate reactively. They discover supplier problems after contracts are signed, relationships are established, and dependencies are locked in.
Proactive risk identification shifts you from crisis management to strategic oversight. You identify vulnerabilities before they manifest as operational problems.
The True Cost of Supply Chain Failures
Financial impacts hit first when supplier issues disrupt operations. Production delays, expedited shipping costs, and emergency supplier changes all drain budgets quickly.
Regulatory exposure grows when you fail to verify supplier compliance. Organizations remain legally responsible for their supply chain partners, particularly in transport and logistics operations.
Safety risks multiply when suppliers cut corners or lack proper certification. Your organization bears responsibility for incidents involving your supply chain, even when they occur at supplier facilities or during contracted transport.
Reputation damage extends beyond individual incidents. Customers and stakeholders expect responsible supply chain management, and failures create lasting trust deficits.
Strategic Advantages of Structured Risk Management
Documented risk assessment processes demonstrate due diligence to regulators and auditors. Your checklist creates evidence that your organization takes supply chain responsibility seriously.
Supplier performance improves when they know you conduct regular risk assessments. The evaluation process itself encourages better practices and transparent communication.
Insurance costs decrease when you demonstrate proactive risk management. Insurers recognize that documented assessment processes reduce claim likelihood and severity.
Strategic relationships strengthen when risk management creates collaborative improvement programs. The best suppliers appreciate thorough evaluation because it demonstrates your commitment to the relationship.
Key Risk Categories to Include in Your Checklist
Structured supply chain risk assessment demands examining multiple risk domains systematically. Each category requires specific evaluation criteria, documentation requirements, and scoring thresholds.
Your checklist should address six primary risk categories that capture the full spectrum of supply chain vulnerabilities. Missing any category leaves gaps that create exposure.
Financial Risk Assessment
Financial stability determines whether suppliers can fulfill long-term commitments. Your checklist needs clear criteria for evaluating supplier financial health.
Review financial statements from the past three years. Look for declining revenue, shrinking margins, increasing debt loads, or negative cash flow that signals distress.
Credit ratings provide third-party validation of financial risk. Require current credit reports and establish minimum acceptable ratings for critical suppliers.
Payment history reveals operational health. Suppliers struggling financially often extend payables, creating risks throughout their supply network.
Insurance coverage protects you from supplier financial failures. Verify adequate liability coverage, business interruption insurance, and product liability protection.
Operational and Service Risk
Operational capability determines whether suppliers can deliver consistently. Your assessment needs to verify capacity, quality systems, and business continuity planning.
Capacity analysis confirms suppliers can meet your volume requirements. Request capacity utilization data and backup production capabilities for critical items.
Quality certifications demonstrate systematic process control. ISO certifications, industry-specific standards, and customer audit results all belong in your evaluation.
Business continuity plans reveal supplier preparedness for disruptions. Request documented plans for key risks like facility damage, equipment failure, or key personnel loss.
Geographic concentration creates vulnerability when multiple suppliers operate in the same region. Assess exposure to natural disasters, political instability, and infrastructure dependencies.
Compliance and Regulatory Risk
Regulatory compliance protects you from legal exposure through your supply chain. Your checklist must verify supplier adherence to relevant standards and regulations.
License verification confirms suppliers hold required operating permits. Transport providers need appropriate vehicle certifications, driver qualifications, and operating authorities.
Safety compliance demonstrates commitment to proper operations. Review incident history, safety training programs, and workplace health and safety management systems.
Environmental compliance matters increasingly to regulators and customers. Verify waste management practices, emissions monitoring, and environmental certification where applicable.
Labor practices require assessment to avoid ethical and legal exposure. Verify fair employment practices, appropriate working conditions, and absence of exploitative practices.
Cybersecurity and Data Security Risk
Digital integration creates cyber vulnerabilities across your supply network. Organizations should define specific controls and integrate cybersecurity objectives into supplier relationships.

Data protection standards need verification when suppliers access your systems or handle sensitive information. Request evidence of security certifications, encryption protocols, and access controls.
Incident response capabilities determine how suppliers handle breaches. Review their incident response plans, backup procedures, and recovery time objectives.
Third-party access controls protect your systems when suppliers connect to your network. Verify authentication requirements, activity monitoring, and regular security assessments.
Software supply chain risks emerge when suppliers provide technology components. Assess their development practices, vulnerability management, and update procedures.
Environmental and Sustainability Risk
Environmental performance increasingly affects business relationships and regulatory compliance. Your checklist needs criteria for assessing supplier environmental practices.
Carbon footprint measurement helps you understand supply chain climate impacts. Request emissions data, reduction targets, and renewable energy usage.
Waste management practices reveal environmental commitment. Verify recycling programs, hazardous material handling, and circular economy participation.
Resource efficiency demonstrates operational sophistication. Assess water usage, energy consumption, and material waste in supplier operations.
Sustainability certifications provide third-party validation. Look for recognized environmental management standards and industry-specific sustainability programs.
Geopolitical and Market Risk
External factors beyond supplier control create supply chain vulnerabilities. Your assessment must consider political stability, economic conditions, and market dynamics.
Political risk analysis examines supplier operating environments. Consider government stability, regulatory predictability, and potential for policy disruption.
Economic conditions affect supplier viability. Monitor inflation, currency stability, labor availability, and market demand in supplier regions.
Trade policy changes create sudden supply chain disruptions. Track tariffs, trade agreements, and export restrictions affecting your supplier base.
Natural disaster exposure requires assessment of geographic vulnerabilities. Identify suppliers in earthquake zones, flood plains, or regions prone to severe weather.
Step 1: Identify and Certify Suppliers
Systematic supplier identification creates the foundation for effective risk management. You cannot manage risks you haven’t identified across your entire supply network.
Start by mapping your complete supplier base. Include direct suppliers providing materials and services, plus critical tier-two suppliers who supply your direct suppliers.
Complete Supplier Mapping
Document every supplier relationship with basic information. Capture company name, location, contact details, and services provided for each supplier.
Classify suppliers by criticality to your operations. Critical suppliers provide unique capabilities, high-volume materials, or services with limited alternatives.
Map supply chain tiers beyond your direct relationships. Understanding tier-two and tier-three suppliers reveals hidden dependencies and concentration risks.
Geographic distribution analysis shows regional concentration risks. Plot supplier locations to identify exposure to regional disruptions.
Certification and Documentation Requirements
Establish clear documentation standards for all suppliers. Required documents should include business registration, operating licenses, insurance certificates, and relevant certifications.
Verify certifications directly with issuing bodies. Don’t accept copies without validation, particularly for safety-critical certifications and regulatory licenses.
Track certification expiration dates in a centralized system. Set renewal reminders for 90 days before expiration to ensure continuous coverage.
Request updated documentation annually as part of your supplier review process. Circumstances change, and your records must reflect current supplier status.
Due Diligence Process
Conduct initial due diligence before establishing new supplier relationships. This assessment should cover all risk categories in your checklist framework.
On-site assessments provide valuable insights for critical suppliers. Visit facilities to verify capabilities, observe operations, and assess management competence.
Reference checks validate supplier claims about performance and reliability. Contact existing customers to understand their experience and any problems encountered.
Background screening protects against fraud and misrepresentation. Verify business ownership, check for litigation history, and confirm financial standing.
Step 2: Monitor Risk Factors Continuously
Risk assessment isn’t a one-time activity. Supplier circumstances change constantly, requiring ongoing monitoring to detect emerging problems before they disrupt operations.

Establishing Monitoring Protocols
Define monitoring frequency based on supplier criticality and risk profile. High-risk suppliers need monthly reviews, while lower-risk relationships can be assessed quarterly.
Identify key indicators for each risk category. Financial metrics, delivery performance, quality issues, and incident reports all signal changing risk levels.
Automated alerts help you respond quickly to emerging problems. Set thresholds for key metrics that trigger immediate review when exceeded.
Create clear escalation procedures when monitoring reveals problems. Define who reviews alerts, makes decisions, and communicates with affected suppliers.
Risk Monitoring Checklist Items
Financial monitoring tracks payment patterns and creditworthiness changes. Late payments, credit limit reductions, or negative news reports all warrant investigation.
Delivery performance metrics reveal operational problems. Track on-time delivery rates, order accuracy, and lead time consistency for early problem detection.
Quality incidents indicate process control issues. Monitor reject rates, customer complaints, and corrective action requests for quality deterioration.
Compliance status requires regular verification. Track license renewals, safety incidents, regulatory inspections, and audit findings.
Market intelligence captures external factors affecting suppliers. Monitor news, industry reports, and economic indicators in supplier regions.
Technology Tools for Risk Monitoring
Centralized platforms streamline risk data management. Automated systems, centralized platforms, and data-driven approaches to supplier management provide beneficial resources for organizations managing large supplier networks.
Integration with supplier systems enables real-time data access. Connect to supplier ERP systems, quality databases, and delivery tracking for current information.
Dashboard reporting provides at-a-glance risk visibility. Visual indicators help managers identify problem suppliers quickly and prioritize attention.
Historical trending reveals patterns that predict future problems. Track risk indicators over time to identify deteriorating suppliers before crises occur.
Step 3: Analyze and Score Supply Chain Risks
Systematic risk analysis transforms monitoring data into actionable insights. Consistent scoring methodologies allow objective comparison across your supplier base.
Your analysis should quantify both likelihood and potential impact for each identified risk. This combination determines overall risk severity and resource allocation priorities.
Risk Scoring Methodology
Establish consistent scoring scales for all risk assessments. Five-point scales work well, rating likelihood and impact from very low to very high.
Define clear criteria for each score level. Specific thresholds prevent subjective ratings that undermine consistency across your supplier base.
Calculate overall risk scores by combining likelihood and impact ratings. Multiply the two factors to generate composite scores that prioritize attention.
Weight risk categories based on your business priorities. Financial and safety risks might carry higher weights than environmental concerns, depending on your industry.
Risk Assessment Framework
Create risk matrices that visualize supplier risk profiles. Plot likelihood against impact to identify suppliers in high-risk quadrants requiring immediate attention.
Establish risk tolerance thresholds for different supplier categories. Critical suppliers might require lower risk acceptance than suppliers with readily available alternatives.
Document assessment rationale to support decisions and demonstrate due diligence. Record evidence examined, scores assigned, and reasoning behind ratings.
Peer comparison reveals relative risk across similar suppliers. Ranking suppliers within categories helps identify outliers and best performers.
Gap Analysis Process
Compare current supplier performance against your requirements. Identify specific gaps between expectations and actual capabilities or practices.
Prioritize gaps based on risk severity and remediation feasibility. Focus resources on closing high-risk gaps that suppliers can reasonably address.
Quantify potential impact of unaddressed gaps. Estimating disruption costs, regulatory exposure, and safety risks helps justify mitigation investments.
Track gap closure progress over time. Regular reassessment shows whether suppliers are improving or whether alternative sources become necessary.
Step 4: Mitigate Risks with Action Plans
Risk identification without action accomplishes nothing. Your checklist must drive specific risk mitigation strategies tailored to each supplier and risk category.
Establishing KPIs, tracking risk status, and regularly reassessing supplier performance are supported practices for maintaining effective risk mitigation programs.

Developing Supplier Action Plans
Create detailed mitigation plans for all high-risk suppliers. Document specific actions, responsible parties, completion deadlines, and success measures.
Collaborate with suppliers on improvement programs. Shared commitment to risk reduction creates stronger results than imposed requirements.
Provide resources to support supplier improvements where appropriate. Technical assistance, training programs, or financial incentives can accelerate risk reduction.
Establish clear consequences for non-compliance. Suppliers need to understand that unaddressed risks will affect business relationships.
Risk Mitigation Strategies by Category
Financial risk mitigation might include payment term adjustments, volume guarantees, or requiring parent company guarantees for struggling suppliers.
Operational risks often require capacity expansion, quality system improvements, or business continuity plan development.
Compliance gaps need corrective action plans with specific milestones. Support suppliers with training, process documentation, or audit preparation.
Cybersecurity improvements may require technology investments. Consider cost-sharing arrangements for security upgrades that benefit your relationship.
Alternative Supplier Development
Source redundancy protects against single-supplier dependencies. Identify backup suppliers for critical items, even if you don’t actively use them.
Multi-sourcing strategies distribute volume across multiple suppliers. This approach reduces concentration risk while maintaining competitive pressure.
Geographic diversification protects against regional disruptions. Develop suppliers in different regions to avoid correlated risks.
Supplier exit strategies need documentation for high-risk relationships. Define triggers that would prompt supplier changes and outline transition processes.
Contractual Risk Controls
Contract terms should reflect identified risks and mitigation requirements. Include specific performance standards, audit rights, and termination provisions.
Insurance requirements transfer certain financial risks to suppliers. Specify minimum coverage levels and require proof of insurance renewal.
Performance bonds protect against supplier failures on critical projects. Consider requiring bonds from suppliers with elevated financial risk.
Indemnification clauses allocate liability for various failure scenarios. Clear contractual language prevents disputes when problems occur.
Essential Checklist Items for Supply Chain Risk Management
A practical risk management checklist needs specific items across all risk categories. This section provides detailed checklist components you can adapt to your organization’s needs.
Supplier Onboarding Checklist
New supplier evaluation should verify business registration and operating licenses in all jurisdictions. Request certified copies of incorporation documents and current good standing certificates.
Financial documentation requirements include three years of financial statements, current credit reports, and bank references. Establish minimum financial thresholds for supplier approval.
Insurance verification needs certificates of currency for liability, workers compensation, and professional indemnity coverage where applicable. Confirm your organization appears as additional insured.
Capability assessment should document production capacity, quality certifications, and relevant industry accreditations. Conduct site visits for critical suppliers.
References from existing customers validate supplier claims. Contact at least three references and ask specific questions about performance and problem resolution.
Ongoing Risk Monitoring Checklist
| Monitoring Area | Check Frequency | Key Indicators |
|---|---|---|
| Financial Health | Quarterly | Payment patterns, credit ratings, financial statements |
| Delivery Performance | Monthly | On-time delivery rate, order accuracy, lead time consistency |
| Quality Metrics | Monthly | Defect rates, customer complaints, corrective actions |
| Compliance Status | Quarterly | License renewals, safety incidents, audit findings |
| Cybersecurity | Semi-annually | Security assessments, breach incidents, system updates |
Compliance Documentation Checklist
Safety certifications require verification of current licenses and training records. Transport providers need driver qualification files, vehicle inspection records, and safety management systems documentation.
Environmental compliance documentation should include waste disposal records, emissions reports, and environmental management system certifications where relevant.
Labor practice verification needs employment contracts, wage records, and workplace safety inspection results. Confirm compliance with local employment law and industry standards.
Quality system documentation must include ISO certifications, quality manual, process documentation, and recent audit reports from customers or third parties.
Cybersecurity Assessment Checklist
Information security policies should address data classification, access controls, encryption standards, and incident response procedures. Request copies of documented policies.
Security certifications like ISO 27001 provide third-party validation of security practices. Verify certification scope covers systems that interact with your organization.
Penetration testing results demonstrate proactive security assessment. Request recent test results and evidence of remediation for identified vulnerabilities.
Business continuity planning needs to cover IT systems specifically. Verify backup procedures, disaster recovery capabilities, and recovery time objectives.
Performance Review Checklist
Annual supplier reviews should examine performance across all risk categories. Schedule formal review meetings with key suppliers to discuss findings and improvement plans.
Scorecard updates need consistent methodology across all suppliers. Rate performance in delivery, quality, compliance, responsiveness, and risk management.
Improvement tracking monitors whether suppliers are addressing identified gaps. Document progress on action items from previous reviews.
Relationship assessment evaluates communication, collaboration, and problem-solving effectiveness. Strong relationships often predict better risk management outcomes.
Risk Escalation Checklist
Define clear triggers that require escalation to management. Critical incidents, major compliance breaches, or significant financial deterioration all warrant immediate attention.
Notification procedures should specify who receives alerts and expected response timeframes. Document escalation paths for different risk severity levels.
Contingency activation criteria determine when to implement backup plans. Establish specific thresholds that trigger alternative supplier engagement.
Communication protocols guide how you interact with suppliers during risk events. Maintain professional relationships while protecting your interests.
Building Your Risk Management Program
Effective supply chain risk management requires systematic processes that become embedded in your operations. The checklist framework outlined here provides structure for identifying, assessing, and mitigating supplier risks before they disrupt your business.
Start by implementing the supplier identification and certification process. Complete mapping of your current supplier base creates visibility into relationships you need to manage.
Develop your monitoring protocols next, focusing on critical suppliers first. Regular assessment of key risk indicators helps you detect problems early when intervention options remain flexible.
Your risk scoring methodology should reflect your organization’s priorities and risk tolerance. Consistent evaluation frameworks enable objective decisions about supplier relationships and resource allocation.
Mitigation strategies must translate assessment into action. Documented plans with clear accountability and deadlines drive actual risk reduction rather than just risk awareness.
The most successful organizations treat supply chain risk management as an ongoing capability, not a periodic project. Your checklist becomes the foundation for sustainable risk oversight that protects operations, ensures compliance, and strengthens supplier relationships over time.