Supplier risk is the threat that a supplier fails to meet obligations, causing operational disruption, financial loss, or reputational damage. To mitigate supplier risk effectively, organizations must establish a systematic process: identify potential risks across financial, operational, compliance, cybersecurity, geopolitical, and reputational categories; assess their likelihood and impact using structured frameworks; prioritize risks based on exposure levels; implement targeted mitigation strategies such as supplier diversification, contractual protections, and continuous monitoring systems; and track performance through real-time dashboards. This approach transforms supplier risk management from reactive firefighting into proactive resilience building, protecting your supply chain against disruptions while maintaining operational continuity.
The Australian supply chain context demands particular attention. From managing compliance risks under regulatory frameworks to coordinating suppliers across multiple geographies, businesses face increasingly interconnected threats. A single supplier failure can cascade through your entire operation.
This guide provides a structured methodology for managing these exposures. You’ll learn how to categorize risks systematically, implement practical assessment frameworks, and deploy monitoring systems that deliver early warning signals. The focus is on building sustainable risk management capabilities that protect your business while supporting supplier relationships.
What Is Supplier Risk and Why It Matters
Supplier risk refers to the potential for disruption when external suppliers fail to deliver products, services, or compliance obligations. These failures create operational bottlenecks, financial exposures, and regulatory violations.
Your supply chain extends beyond direct relationships. Tier 2 and tier 3 suppliers introduce hidden dependencies. When a component manufacturer experiences financial distress, your tier 1 supplier may lack alternatives. This ripple effect amplifies disruption.
Supplier risk management is the systematic process of identifying, assessing, and controlling these exposures. It transforms reactive problem-solving into proactive resilience building. Organizations that implement structured supplier risk management protect continuity while maintaining competitive advantage.
The Cost of Unmanaged Supplier Risk
Unmanaged supplier risk creates measurable business impact. Production delays disrupt customer commitments. Quality failures trigger recalls and warranty claims. Compliance failures generate regulatory penalties.
Financial stability issues deserve particular attention. When suppliers face cash flow problems, they reduce quality controls or delay deliveries. Some cease operations entirely. This leaves buyers scrambling for alternatives during critical periods.
Reputational damage extends beyond immediate disruption. If your supplier engages in unethical practices, your brand suffers association damage. Customers increasingly expect supply chain transparency and responsible sourcing.
The Business Case for Proactive Risk Mitigation
Proactive supplier risk management delivers measurable returns. Organizations reduce emergency procurement costs by maintaining qualified backup suppliers. They avoid production stoppages through early warning systems. They protect margins by preventing quality failures.
Risk mitigation also strengthens supplier relationships. When you collaborate on risk assessments, suppliers recognize your commitment to mutual success. This builds trust and improves communication during challenging periods.
Technology solutions amplify these benefits. Modern platforms automate supplier monitoring, track compliance certifications, and aggregate risk data. This enables procurement teams to focus on strategic interventions rather than administrative tracking.
Understanding the Categories of Supplier Risk
Supplier risks span multiple domains. Each category requires specific assessment methods and mitigation strategies. Comprehensive risk management addresses all categories systematically.
Financial Risk
Financial risk emerges when suppliers lack adequate capital, liquidity, or creditworthiness. Warning signs include delayed invoice payments, reduced credit limits, or deteriorating financial ratios. These conditions often precede supplier failure.
Financial stability assessment requires reviewing financial statements, credit reports, and payment histories. Look for declining profitability, increasing debt ratios, or negative cash flow. These indicators suggest elevated risk.
Small and medium suppliers warrant particular attention. They typically lack financial buffers to weather demand fluctuations or payment delays. A single large customer loss can threaten their viability.
Operational Risk
Operational risk encompasses production capacity, quality control, and logistics capabilities. Suppliers with aging equipment, inadequate maintenance programs, or insufficient quality systems introduce performance variability. This creates delivery uncertainty.
Capacity constraints emerge during demand surges. If your supplier operates at 95% capacity, they cannot accommodate growth or recover from disruptions. This vulnerability affects your ability to meet customer commitments.
Geographic concentration amplifies operational risk. When multiple suppliers operate in the same region, natural disasters or infrastructure failures impact all simultaneously. This creates correlated exposures.
Compliance and Regulatory Risk
Compliance risk arises when suppliers fail to meet legal, regulatory, or contractual obligations. This includes workplace safety violations, environmental breaches, or certification lapses. These failures expose buyers to regulatory action and reputational damage.
Regulatory environments evolve continuously. New requirements for data protection, environmental reporting, or ethical sourcing change compliance obligations. Suppliers struggling to adapt introduce risk.
Audit and certification status provides compliance visibility. Regular reviews verify that suppliers maintain required licenses, permits, and quality certifications. Lapses indicate control weaknesses.
Cybersecurity Risk
Cybersecurity threats from suppliers represent growing exposure. When suppliers access your systems, data, or networks, they create potential attack vectors. Inadequate supplier security controls enable data breaches and system compromises.
Third-party cybersecurity assessments evaluate supplier security posture. Review their access controls, encryption practices, and incident response capabilities. Suppliers with weak security introduce unacceptable risk.
Contractual protections establish security requirements and breach notification obligations. These provisions enable rapid response when security incidents occur. They also clarify liability allocation.
Geopolitical Risk
Geopolitical risk includes trade restrictions, political instability, and policy changes affecting supplier operations. Tariffs, export controls, or border closures disrupt supply flow. These events often occur without warning.
Supplier location mapping identifies geographic concentrations. When critical suppliers cluster in politically unstable regions, your exposure increases. Diversification across geographies reduces this vulnerability.
Geopolitical monitoring services track emerging risks in supplier regions. Early awareness enables proactive mitigation before disruptions materialize. This provides time to develop alternatives.
Reputational Risk
Reputational risk emerges when supplier actions damage your brand. Labor practice violations, environmental incidents, or ethical breaches create negative associations. Public perception treats supplier failures as buyer responsibility.
Ethical sourcing programs establish standards for supplier conduct. These requirements address labor conditions, environmental practices, and business ethics. Regular audits verify compliance.
Transparency initiatives demonstrate responsible supply chain management. Publishing supplier lists and audit results builds stakeholder confidence. This approach transforms potential liability into competitive advantage.
Building Your Supplier Risk Assessment Framework
Structured risk assessment transforms subjective judgment into systematic evaluation. This process identifies vulnerabilities before they create disruption. It also prioritizes mitigation resources toward highest-impact exposures.
Step 1: Identify All Potential Risks
Risk identification begins with supply chain mapping. Document all suppliers, including tier 2 and tier 3 relationships. This visibility reveals hidden dependencies and concentration risks.
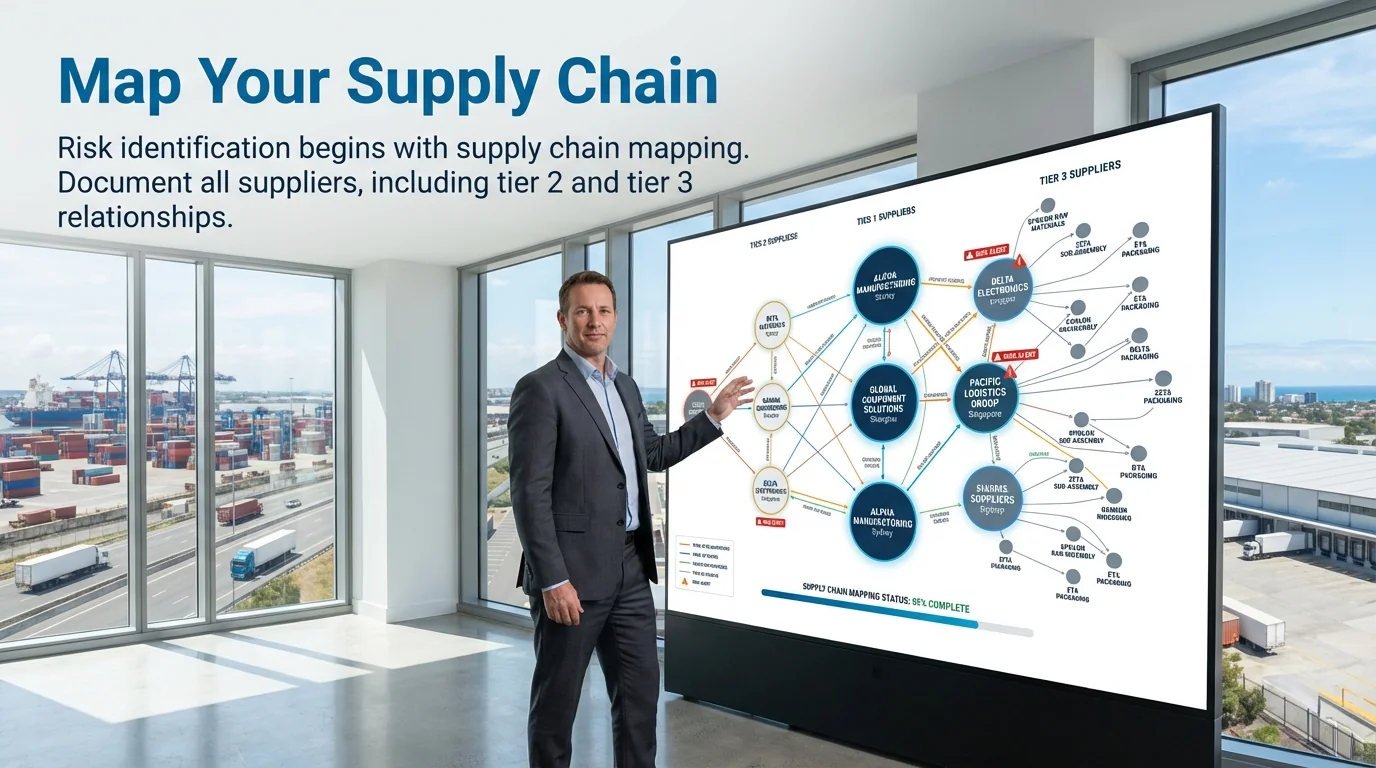
Conduct risk workshops with cross-functional teams. Procurement, operations, quality, and finance each provide unique perspectives. This collaboration surfaces risks that individual functions might overlook.
Use standardized risk categories to structure identification. Review financial, operational, compliance, cybersecurity, geopolitical, and reputational dimensions systematically. This framework prevents blind spots.
Step 2: Assess Risk Likelihood and Impact
Risk assessment quantifies both probability and consequence. Likelihood considers historical patterns, industry trends, and supplier-specific factors. Impact evaluates operational, financial, and reputational effects.
Create a risk scoring matrix that combines likelihood and impact. This tool enables consistent evaluation across suppliers. It also facilitates comparison and prioritization.
Gather supporting evidence for assessments. Financial statements, audit reports, quality metrics, and delivery performance provide objective data. This evidence-based approach reduces assessment bias.
Step 3: Prioritize Risks for Mitigation
Not all risks warrant equal attention. Prioritization focuses resources on exposures with highest potential impact. This approach balances risk reduction against mitigation costs.
High-likelihood, high-impact risks demand immediate action. These critical exposures threaten business continuity. Mitigation becomes a priority investment.
Consider supplier criticality in prioritization. Sole-source suppliers for essential components warrant intensive risk management regardless of current risk scores. Their failure immediately disrupts operations.
Step 4: Document Assessment Results
Formal documentation captures assessment findings and decisions. This creates accountability and enables tracking over time. It also provides audit trails for compliance purposes.
Risk registers consolidate assessment data in standardized formats. Each entry includes risk description, likelihood, impact, priority, and assigned owner. This centralized view supports program management.
Share assessment results with relevant stakeholders. Transparency builds organizational awareness and supports resource allocation decisions. It also demonstrates risk management maturity to auditors and customers.
Implementing Practical Supplier Risk Mitigation Strategies
Effective mitigation combines prevention, protection, and response capabilities. The following strategies address different risk categories and organizational contexts. Select approaches that align with your specific risk profile and business requirements.
Strategy 1: Diversify Your Supplier Base
Supplier diversification reduces concentration risk by spreading exposure across multiple sources. Dual or multi-sourcing strategies ensure continuity when individual suppliers experience disruption.
Identify critical components or services dependent on single suppliers. Develop qualification criteria for alternatives. Begin relationship building before you need backup capacity.
Balance diversification against complexity costs. Managing multiple supplier relationships requires additional resources. Focus diversification on highest-risk or highest-impact exposures where the investment delivers clear value.
Strategy 2: Strengthen Contractual Protections
Contracts establish performance expectations, quality standards, and compliance obligations. Well-structured agreements also allocate risks between parties and define remedies for failures.
Contractual risk transfer can shift certain exposures onto the supplier, including insurance requirements, indemnification provisions, and liability caps. These protections limit financial exposure when failures occur.

Include termination rights for material breaches. This flexibility enables rapid response to deteriorating supplier performance. Early exit prevents extended exposure to failing suppliers.
Strategy 3: Implement Continuous Monitoring Systems
Continuous monitoring detects emerging risks before they escalate. Real-time tracking of supplier performance, financial health, and compliance status enables proactive intervention.
ISO 31000 enables continuous monitoring for supplier-related risks, providing a standardized framework for risk management processes. This approach supports systematic oversight.

Monitor key performance indicators including on-time delivery, quality metrics, and responsiveness. Declining trends signal potential issues. Early awareness creates time for corrective action or supplier changes.
Strategy 4: Develop Supplier Capability Programs
Supplier development improves reliability by strengthening partner capabilities. This collaborative approach reduces risk while building competitive advantage. Strong suppliers perform more consistently.
Provide technical assistance for quality improvement, process optimization, or technology adoption. These investments enhance supplier performance while deepening relationships. Improved capabilities reduce operational risk.
Establish formal improvement programs with measurable objectives. Track progress through regular reviews. Recognize achievements to reinforce positive performance.
Strategy 5: Build Inventory and Capacity Buffers
Strategic buffers protect against short-term disruptions. Safety stock of critical components ensures production continuity during supplier delays. Buffer capacity provides alternatives when primary suppliers cannot meet demand.
Calculate optimal buffer levels based on risk assessment and business impact. High-criticality items with long lead times warrant larger buffers. Standard components with multiple sources require less protection.
Balance buffer costs against disruption risks. Excessive inventory ties up capital and increases obsolescence risk. Target protection at highest-priority exposures.
Strategy 6: Establish Business Continuity Plans
Business continuity planning prepares response protocols for supplier failures. These plans define roles, decision criteria, and action steps. Pre-planning enables rapid response during crises.
Identify trigger points for plan activation. Clear thresholds prevent delays during actual disruptions. Automate notifications when triggers occur.
Test continuity plans through exercises and simulations. Practice reveals gaps and builds organizational capability. Regular testing ensures plans remain current as supply chains evolve.
Strategy 7: Foster Cross-Functional Collaboration
Collaboration across departments ensures alignment on risk metrics and enables coordinated response. Procurement, operations, quality, finance, and legal each contribute essential perspectives to effective risk management.

Establish regular risk review meetings with cross-functional representation. These forums enable information sharing and coordinated decision-making. Shared visibility improves response effectiveness.
Create clear escalation paths for emerging risks. Define authority levels for different mitigation actions. This structure enables rapid response without bureaucratic delays.
Leveraging Technology for Supplier Risk Management
Technology solutions transform supplier risk management from manual processes into automated, data-driven programs. Modern platforms aggregate risk data, automate monitoring, and enable proactive intervention. These capabilities scale risk management across large supplier networks.
Risk Management Software Capabilities
Specialized supply chain risk management software provides centralized platforms for supplier oversight. These systems integrate data from multiple sources, including financial providers, news feeds, and internal performance systems.
AI-powered risk management tools enable real-time risk scoring that adapts as conditions change. Automated alerts notify stakeholders when risk thresholds are exceeded. This proactive capability enables timely intervention.

Look for platforms that support your specific requirements. Core features include supplier onboarding, due diligence workflows, continuous monitoring, and compliance tracking. Advanced capabilities include predictive analytics and scenario modeling.
Data Integration and Analytics
Effective risk management requires integrating data from diverse sources. Financial data providers offer credit monitoring and bankruptcy predictions. News aggregators track operational incidents and regulatory actions. Internal systems provide performance metrics.
Analytics capabilities transform raw data into actionable insights. Dashboards visualize risk trends and highlight priority exposures. Predictive models forecast potential failures before they occur.
Ensure data quality through validation and cleansing processes. Inaccurate data undermines risk assessment accuracy. Establish governance procedures that maintain data integrity over time.
Automation Opportunities
Automation reduces manual effort while improving consistency. Automated supplier onboarding collects required documentation and verifies certifications. Scheduled assessments trigger periodic risk reviews without manual intervention.
Workflow automation routes tasks to appropriate reviewers based on risk levels. High-risk suppliers receive enhanced scrutiny. Low-risk suppliers follow streamlined processes. This risk-based approach optimizes resource allocation.
Alert automation notifies stakeholders when monitoring systems detect concerning changes. Real-time notifications enable rapid response to emerging issues. This proactive capability prevents minor issues from escalating.
Implementation Considerations
Technology implementation requires careful planning. Begin by documenting current processes and identifying pain points. This baseline guides solution selection and configuration.
Engage stakeholders throughout implementation. User input ensures the system supports actual workflows. Change management activities build adoption and capability.
Plan for integration with existing systems. Risk management platforms should connect to procurement, ERP, and quality systems. These integrations eliminate duplicate data entry and ensure consistency.
Establishing Continuous Monitoring and Improvement Processes
Supplier risk management is not a one-time exercise. Effective programs establish ongoing monitoring that tracks performance, detects emerging risks, and validates mitigation effectiveness. Continuous improvement refines approaches based on experience and changing conditions.
Designing Your Monitoring Framework
Monitoring frameworks define what to track, how frequently to assess, and when to escalate. This structure ensures consistent oversight across your supplier base.
Segment suppliers based on risk profile and business impact. Critical suppliers require intensive monitoring with frequent assessments. Low-risk suppliers follow simplified protocols with less frequent reviews. This tiered approach balances thoroughness against resource constraints.
Define specific metrics for each risk category. Financial monitoring tracks payment terms and credit ratings. Operational monitoring measures delivery performance and quality metrics. Compliance monitoring verifies certifications and audit findings.
Establishing Review Cycles
Regular review cycles ensure risks are reassessed as conditions change. High-risk suppliers warrant monthly or quarterly reviews. Medium-risk suppliers follow semi-annual assessments. Low-risk suppliers require annual reviews at minimum.
Trigger event-based reviews when significant changes occur. Supplier mergers, leadership changes, or financial distress warrant immediate reassessment. Major operational incidents or compliance violations also trigger reviews.
Document review findings and track changes over time. Trend analysis reveals whether risks are improving or deteriorating. This longitudinal view supports strategic decisions about supplier relationships.
Building Feedback Loops
Feedback loops capture lessons from disruptions and near-misses. After-action reviews identify root causes and assess response effectiveness. These insights drive continuous improvement.
Share learnings across the organization. When one team experiences a supplier issue, others benefit from understanding what happened and how it was resolved. This knowledge transfer builds organizational capability.
Update risk assessments and mitigation strategies based on experience. As you learn which indicators predict problems most reliably, refine your monitoring approach. This evolution improves effectiveness over time.
Maintaining Program Governance
Governance structures provide oversight and ensure consistent execution. Establish clear roles and responsibilities for risk management activities. Define who conducts assessments, who reviews findings, and who authorizes mitigation investments.
Create regular reporting to executive leadership. Risk management performance metrics demonstrate program value and support resource allocation. Transparency builds organizational commitment.
Conduct periodic program audits to verify compliance with policies and procedures. Independent review identifies gaps and improvement opportunities. Regular audits maintain program rigor.
Measuring Success and Optimizing Your Approach
Effective supplier risk management delivers measurable business value. Tracking the right metrics demonstrates impact and guides optimization. This evidence-based approach ensures continuous program improvement.
Key Performance Indicators
Risk management KPIs fall into three categories: exposure metrics, process metrics, and outcome metrics. Each provides different insights into program effectiveness.
Exposure metrics quantify your risk profile. Track the number of high-risk suppliers, concentration in critical categories, and overall risk score trends. Improving exposure metrics indicate successful risk reduction.
Process metrics measure program execution. Monitor assessment completion rates, mitigation plan implementation, and monitoring coverage. These operational measures ensure consistent program delivery.
Business Impact Measurement
Outcome metrics demonstrate business value. Track supply disruption frequency, emergency procurement costs, and quality incident rates. Reductions in these measures prove program effectiveness.
Calculate avoided costs from early risk detection. When monitoring systems identify supplier issues before they cause disruption, quantify the value of prevented losses. This measurement builds the business case for continued investment.
Monitor supplier relationship quality. Strong risk management programs improve communication and collaboration. Measure this through supplier satisfaction surveys and relationship health assessments.
Program Optimization
Use performance data to identify optimization opportunities. If certain risk categories consistently cause problems, enhance those assessment capabilities. If specific mitigation strategies prove most effective, expand their use.
Benchmark your program against industry standards and peer practices. External perspectives reveal improvement opportunities. Global supply chain risk mitigation strategies offer additional frameworks for consideration.
Stay current on emerging risks and evolving best practices. Supply chain risks change as business environments evolve. Regular program updates ensure your approach remains effective against current threats.
Building Resilient Supplier Relationships
Your supplier risk management program protects business continuity while strengthening supply chain performance. The systematic approach outlined here transforms reactive problem-solving into proactive resilience building.
Start by assessing your current state. Map your critical suppliers, identify concentration risks, and evaluate existing controls. This baseline reveals priority improvement areas.
Implement monitoring systems that provide early warning of emerging issues. Technology solutions scale these capabilities across large supplier networks. Real-time visibility enables proactive intervention.
Remember that effective risk management requires systematic frameworks and continuous improvement. Regular assessment cycles, cross-functional collaboration, and performance measurement ensure sustained effectiveness.
The most successful programs balance risk control with supplier partnership. Strong relationships built on transparency and collaboration weather disruptions more effectively than purely transactional arrangements. Invest in supplier capability while maintaining appropriate oversight.
Take action today. Review your highest-risk supplier relationships. Verify that monitoring systems are in place. Confirm that mitigation strategies align with current exposures. These immediate steps begin building the resilience your supply chain requires.